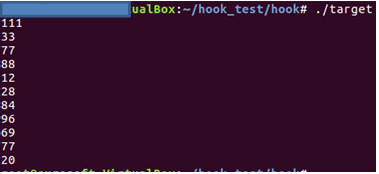
This is an
example of hooking a class function.
This article doesn't have many examples of hooking c ++ classes.
The
following code:
Class
TestClass {
Public:
…
int myPrintf(const
std::string & id, const int & value);
…
}
Hook
code:
int TestClass::myPrintf(const std::string & id, const int & value) {
typedef int
(TestClass::*HookFunction)(const std::string & id,
const int & value);
static HookFunction orgMethod = 0;
if (orgMethod == 0) {
void *tmpPtr = dlsym(RTLD_NEXT,
"Mangling Name");
memcpy(&orgMethod, &tmpPtr,
sizeof(void *));
}
int orgRetValue;
orgRetValue = (this->*orgMethod)(id,
value);
return orgRetValue;
#C #C++ #Linux #Embedded #Hooking Example #Hooking #Class Hooking